Although there are many firewall technologies, but generally speaking can be divided into "packet filtering type" and "application agent type" two broad categories. The former is represented by the Israeli Checkpoint firewall and the Cisco PIX firewall of the United States. The latter is represented by the Gauntlet firewall of NAI Inc. of the United States.
(1). The packet filtering packet filtering firewall works at the network layer and transport layer of the OSI network reference model. It determines whether or not to allow traffic based on the source address, destination address, port number, and protocol type of the packet header. Only packets that meet the filter criteria are forwarded to the corresponding destination, and the remaining packets are discarded from the data stream.
Packet filtering is a universal, cheap and effective security measure. The reason why it is universal is that it does not take special treatment for each specific network service and applies to all network services. The reason for its low price is that most routers provide packet filtering, so most of these firewalls are routers. Integrated; it is effective because it can largely meet the vast majority of corporate security requirements.
In the development of the entire firewall technology, there are two different versions of packet filtering technology, called "first-generation static packet filtering" and "second-generation dynamic packet filtering."
â— The first generation of static packet filter type firewalls These types of firewalls are generated almost at the same time as the routers. They examine each packet according to defined filtering rules to determine whether it matches a packet filter rule. Filtering rules are based on the header information of the packet. The header information includes an IP source address, an IP destination address, a transmission protocol (TCP, UDP, ICMP, etc.), a TCP/UDP destination port, an ICMP message type, and the like.
â— Second-generation dynamic packet filter type firewall This kind of firewall adopts the method of dynamically setting packet filter rules to avoid the problems of static packet filtering. This technology later developed into Stateful Inspection technology. Firewalls using this technique track each connection established through it and dynamically add or update entries in the filter rules as needed.
The advantage of the packet filtering approach is that it does not require changes to the client and host applications because it operates at the network and transport layers, independent of the application layer. But its weaknesses are also obvious: the basis of filter discrimination is only the limited information of the network layer and transport layer, so various security requirements cannot be fully satisfied; in many filters, the number of filter rules is limited, and with the rules As the number increases, performance will be greatly affected; due to the lack of contextual information, protocols such as UDP and RPC (Remote Procedure Call) cannot be effectively filtered; in addition, most auditors lack auditing and alerting mechanisms. According to the header information, the user identity can not be verified, it is vulnerable to "address spoofing" attacks. The requirements for the quality of safety management personnel are high. When establishing safety rules, we must have a deeper understanding of the agreement itself and its role in different applications. Therefore, filters are usually used in conjunction with application gateways to form a firewall system.
(2). The Application Proxy type of application proxy firewall is the top layer of OSI, namely the application layer. Its characteristic is that it completely “blocks†the network communication flow, and through the preparation of a special agent program for each application service, the role of monitoring and controlling the application layer communication flow is achieved. Its typical network structure is shown in the figure.
In the development of the agent-based firewall technology, it has also experienced two different versions, namely: the first generation of application gateway-type proxy fire prevention and the second-generation adaptive proxy firewall.
The first generation of Application Gateway type firewalls participate in the entire process of a TCP connection through a proxy (Proxy) technology. Packets sent from the inside through such a firewall are treated as if they originated from the firewall's external network card, which can hide the internal network structure. This type of firewall is recognized by cybersecurity experts and the media as the most secure firewall. Its core technology is proxy server technology.
The second-generation adaptive proxy firewall is a new type of firewall that has been widely used in recent years. It can combine the security of proxy-type firewalls and the high speed of packet-filtering firewalls to increase the performance of proxy-based firewalls by more than 10 times without sacrificing security. There are two basic elements that make up this type of firewall: Adaptive Proxy Server and Dynamic Packet Filter.
There is a control channel between "adaptive proxy server" and "dynamic packet filter". When configuring the firewall, the user only needs to set the required service type, security level, and other information through the corresponding Proxy management interface. Then, the adaptive agent can decide whether to use the proxy service to request from the application layer proxy or to forward the packet from the network layer according to the user's configuration information. If it is the latter, it will dynamically notify the packet filter of the increase and decrease of filtering rules to meet the user's dual requirements for speed and security.
The most prominent advantage of proxy-type firewalls is security. Because it works at the highest level, it can filter and protect any layer of data traffic in the network, instead of filtering data at the network layer as it does for packet filtering.
In addition, the proxy-type firewall adopts a proxy mechanism. It can establish a dedicated proxy for each type of application service. Therefore, the communication between the internal and external networks is not direct, and it needs to be audited by the proxy server before passing. The proxy server acts as a connection and does not give any opportunity for any internal session or external network computer to directly communicate. This prevents intruders from using data-driven attack methods to invade the internal network.
The biggest drawback of the proxy firewall is that the speed is relatively slow. When the user's throughput requirements for the internal and external network gateways are relatively high, the proxy firewall becomes a bottleneck between the internal and external networks. That is because firewalls need to establish specialized proxy services for different network services. It takes time for their own agents to establish connections for internal and external network users. This has negative impact on system performance, but it is usually not obvious.
(1). The packet filtering packet filtering firewall works at the network layer and transport layer of the OSI network reference model. It determines whether or not to allow traffic based on the source address, destination address, port number, and protocol type of the packet header. Only packets that meet the filter criteria are forwarded to the corresponding destination, and the remaining packets are discarded from the data stream.
Packet filtering is a universal, cheap and effective security measure. The reason why it is universal is that it does not take special treatment for each specific network service and applies to all network services. The reason for its low price is that most routers provide packet filtering, so most of these firewalls are routers. Integrated; it is effective because it can largely meet the vast majority of corporate security requirements.
In the development of the entire firewall technology, there are two different versions of packet filtering technology, called "first-generation static packet filtering" and "second-generation dynamic packet filtering."
â— The first generation of static packet filter type firewalls These types of firewalls are generated almost at the same time as the routers. They examine each packet according to defined filtering rules to determine whether it matches a packet filter rule. Filtering rules are based on the header information of the packet. The header information includes an IP source address, an IP destination address, a transmission protocol (TCP, UDP, ICMP, etc.), a TCP/UDP destination port, an ICMP message type, and the like.
â— Second-generation dynamic packet filter type firewall This kind of firewall adopts the method of dynamically setting packet filter rules to avoid the problems of static packet filtering. This technology later developed into Stateful Inspection technology. Firewalls using this technique track each connection established through it and dynamically add or update entries in the filter rules as needed.
The advantage of the packet filtering approach is that it does not require changes to the client and host applications because it operates at the network and transport layers, independent of the application layer. But its weaknesses are also obvious: the basis of filter discrimination is only the limited information of the network layer and transport layer, so various security requirements cannot be fully satisfied; in many filters, the number of filter rules is limited, and with the rules As the number increases, performance will be greatly affected; due to the lack of contextual information, protocols such as UDP and RPC (Remote Procedure Call) cannot be effectively filtered; in addition, most auditors lack auditing and alerting mechanisms. According to the header information, the user identity can not be verified, it is vulnerable to "address spoofing" attacks. The requirements for the quality of safety management personnel are high. When establishing safety rules, we must have a deeper understanding of the agreement itself and its role in different applications. Therefore, filters are usually used in conjunction with application gateways to form a firewall system.
(2). The Application Proxy type of application proxy firewall is the top layer of OSI, namely the application layer. Its characteristic is that it completely “blocks†the network communication flow, and through the preparation of a special agent program for each application service, the role of monitoring and controlling the application layer communication flow is achieved. Its typical network structure is shown in the figure.
In the development of the agent-based firewall technology, it has also experienced two different versions, namely: the first generation of application gateway-type proxy fire prevention and the second-generation adaptive proxy firewall.
The first generation of Application Gateway type firewalls participate in the entire process of a TCP connection through a proxy (Proxy) technology. Packets sent from the inside through such a firewall are treated as if they originated from the firewall's external network card, which can hide the internal network structure. This type of firewall is recognized by cybersecurity experts and the media as the most secure firewall. Its core technology is proxy server technology.
The second-generation adaptive proxy firewall is a new type of firewall that has been widely used in recent years. It can combine the security of proxy-type firewalls and the high speed of packet-filtering firewalls to increase the performance of proxy-based firewalls by more than 10 times without sacrificing security. There are two basic elements that make up this type of firewall: Adaptive Proxy Server and Dynamic Packet Filter.
There is a control channel between "adaptive proxy server" and "dynamic packet filter". When configuring the firewall, the user only needs to set the required service type, security level, and other information through the corresponding Proxy management interface. Then, the adaptive agent can decide whether to use the proxy service to request from the application layer proxy or to forward the packet from the network layer according to the user's configuration information. If it is the latter, it will dynamically notify the packet filter of the increase and decrease of filtering rules to meet the user's dual requirements for speed and security.
The most prominent advantage of proxy-type firewalls is security. Because it works at the highest level, it can filter and protect any layer of data traffic in the network, instead of filtering data at the network layer as it does for packet filtering.
In addition, the proxy-type firewall adopts a proxy mechanism. It can establish a dedicated proxy for each type of application service. Therefore, the communication between the internal and external networks is not direct, and it needs to be audited by the proxy server before passing. The proxy server acts as a connection and does not give any opportunity for any internal session or external network computer to directly communicate. This prevents intruders from using data-driven attack methods to invade the internal network.
The biggest drawback of the proxy firewall is that the speed is relatively slow. When the user's throughput requirements for the internal and external network gateways are relatively high, the proxy firewall becomes a bottleneck between the internal and external networks. That is because firewalls need to establish specialized proxy services for different network services. It takes time for their own agents to establish connections for internal and external network users. This has negative impact on system performance, but it is usually not obvious.
This style is a Vacuum Cleaner that is 2 in 1. What is 2 in 1 that is not only a Bagged Vacuum Cleaner,but also a Bagless Vacuum Cleaner. When it's a bagged vacuum cleaner,it has the functions like other bagged vacuum cleaners. When it's a bagless vacuum cleaner,it also has functions like other bagless vacuum cleaners. It is a vacuum cleaner that has high suction power,low noise,HEPA filter and so on. In a word,it is a high-end vacuum cleaner. Hope you will like it,now please see some pictures blow.
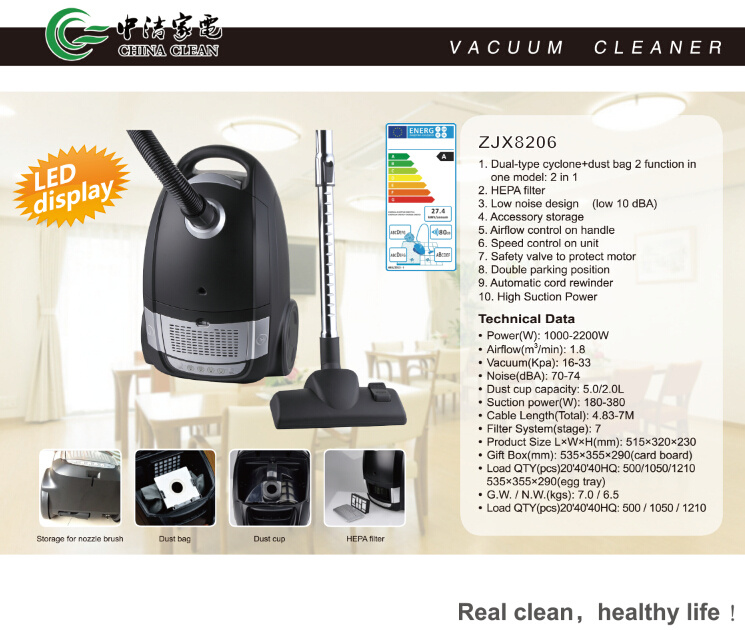
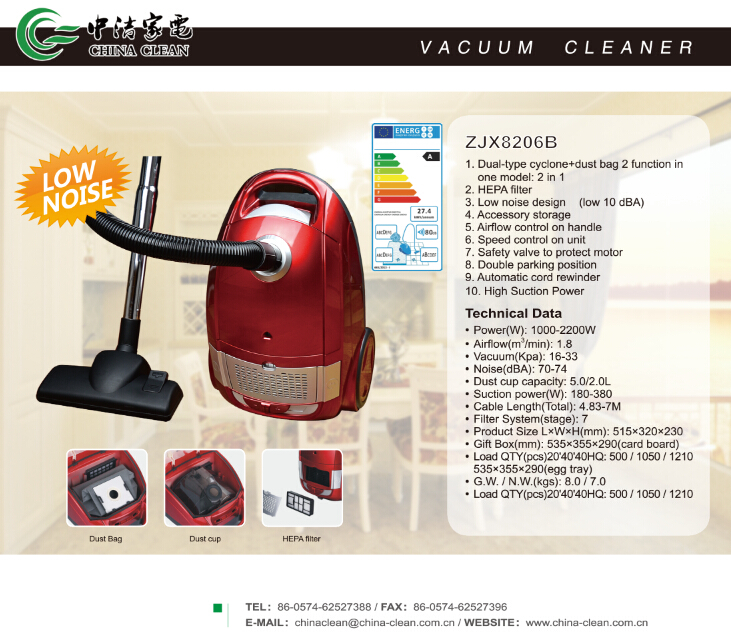
Bag & Bagless(2 In 1) Vacuum Cleaner
Bagless Vacuum Cleaner, 2 In 1 Vacuum Cleaner, Bag Vacuum Cleaner
Ningbo ChinaClean Household Appliances Manufacture Co., Ltd. , http://www.chinaclean-elec.com