Tag: Intelligent Video Full Analog System
This article refers to the address: http://
1. Squandering flowers and fascinating eyes
As we all know, the development of video surveillance system has experienced the development of the first generation of full analog system, the second generation of semi-digital system, the third generation of all-digital system (network camera and video server), now the whole The industry is brewing a new revolution in video surveillance - intelligent video surveillance.
Video analytics technology has developed rapidly in recent years. Whether it is from the publicity of the media or from large and small exhibitions, people seem to feel that "smart video, video analysis, IVS/CV" has come to us. The concept of a few years ago has become a reality, and it seems to be subverting the traditional monitoring methods and subverting people's monitoring concepts. Indeed, video analytics technology has already entered China from the concept, from the laboratory, from Europe and the United States, Qinghai-Tibet Railway, Metro Line 5, Line 13, Civil Aviation Center, etc., have already had multiple video analysis products in the day and night Work; intrusion, packet loss, anti-tailing, etc. are applied.
Recently, a research report from the IMS Research survey agency predicts that the video content analysis market will be unprecedentedly prosperous in the next five years, from $6.77 million in 2004 to $83.92 million in 2009, an increase of 65.5%. Many developers are quite optimistic about their prospects.
2. Dial the cloud to the fog and save it.
The background generated by video analysis is very simple. One of them is security application. When security personnel face ten, one hundred or one thousand cameras, they cannot really prevent or intervene when risks or alarms occur. Most of them rely on post-reproduction related videos. The second is non-security applications, such as business flow statistics, prevention of plagiarism and so on. The idea is to transfer risk analysis and behavioral identification to a computer or chip, so that security personnel can be freed from the work of the "dead stare" monitor. When the computer finds a problem, an alarm is generated and the security personnel respond.
As the next wave of traditional CCTV surveillance systems, the arrival of digital video systems has undoubtedly marked the entry of a 24*7 all-weather surveillance system into a more efficient new era. However, there are still some serious problems. For hours, staring at multiple monitors that typically show static walls and guardrails, even the most trained security personnel face the challenge of attention. This problem is compounded by objective conditions such as darkness or bad weather conditions. As the number of cameras and closed-circuit television monitors deployed in digital surveillance networks continues to increase, the ability of security personnel to effectively view images of all points on the network has actually declined due to information overload. Obviously, security personnel urgently need a more intelligent system to play the role of an automatic “electronic eye†in order to accurately detect potential intruders, suspicious targets and other security violations, thus enabling security personnel. It will be able to make quick and informed decisions and real-time responses to events.
Video analysis technology uses computer image visual analysis technology to analyze and track the objects appearing in the camera scene by separating the background and the target in the scene. According to the function of video content analysis, the user can preset different alarm rules in different camera scenes. Once the target violates the predefined rules in the scene, the system will automatically issue an alarm, and the monitoring workstation automatically pops up the alarm information. A warning tone is issued, and the user can click on the alarm information to implement the scene reorganization of the alarm and take relevant measures.
3. Intelligent analysis of non-universal
Perhaps, when you hear the word "smart", some people will immediately associate high-tech artificial intelligence software to monitor suspicious behavior. Yes, IVS is indeed an excellent monitoring tool, but it is not omnipotent. In order to achieve the best performance of the IVS, in addition to not being able to select the wrong application site, the user must also formulate a corresponding upgrade strategy according to specific needs, taking into account different standard protocols. Only in this way can we do our best.
Regardless of the extent to which IVS software has progressed, there are always limitations. The current IVS technical standards are lacking and have not been matured and widely used. Take "unattended baggage" as an example. There are too many doubts between the manufacturer's explanation and the actual function. Currently, normal and more realistic video analysis features include border protection, intrusion detection, crowd and route control, directional alarms, license plate recognition, legacy object detection, movement and overflow monitoring. Second, in non-prosperous locations, more mature applications include demographics, vehicle statistics, and stay tracking.
In the case of extreme busyness or excessive distance, such as counting of people, facial recognition, pickpocket or theft monitoring, and object tracking are difficult to accomplish. The best time to count is when people enter or leave an area, pass through corridors and passages, and walk side by side. When the crowd is crowded and staggered, the software cannot accurately identify and analyze the image because the image taken is blurred, resulting in a very high false positive rate.
Another limitation is its facial recognition function. As we all know, camouflage may make this function not reliable. At present, not only automatic threat monitoring, but also the ability of IVS to monitor pickpockets or theft is not too optimistic. Similarly, tracking targets in a very busy environment is quite difficult. For example, in large underground stations where thousands of people enter, stay, pick up or drop their luggage, false alarms are unusually useless and useless.
4. Traditional intelligence is suitable for both
In summary, since the development of traditional video surveillance has encountered bottlenecks, and the emerging intelligent monitoring has limitations, how will end users choose? How do we provide users with the best solution? Tianjin Tiandi Weiye has deep user needs. Analysis, combined with the status quo of intelligent monitoring technology at home and abroad, provides users with multiple complete and complete solutions for different environments, that is, the combination of traditional video surveillance and intelligent monitoring technology.
First, because of the wide variety of applications, intelligent video surveillance will show a variety of product forms, including:
(1) The intelligent processing algorithm is loaded on the network video server (NVS/DVS) to form an intelligent video server;
(2) The intelligent processing algorithm is loaded in the hard disk recorder to form an intelligent analysis hard disk recorder;
(3) Intelligent processing algorithms will also implement centralized analysis and processing capabilities in a software-only manner along with video surveillance management software.
Solution 1: For traditional analog monitoring (built or newly built), select key and high-risk monitoring targets and locations, analyze the part of the image, actively monitor, and send the warning and alarm to the analog matrix and DVR in real time. Switch and record, select Intelligent Video Server (IVS BOX), the solution is as shown:
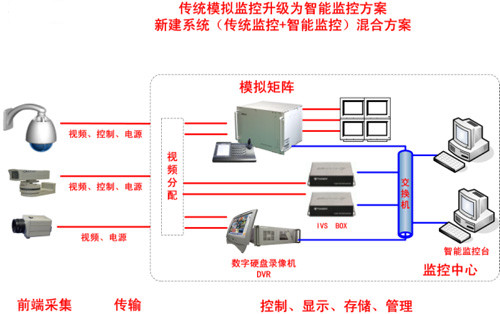
Solution 2: For traditional analog monitoring (built or newly built), select key and high-risk monitoring targets and locations, perform analysis functions for this part of the image, actively monitor, and send warnings and alarms to the analog matrix and DVR in real time. Switch and record, select intelligent analysis DVR, the solution is as shown:
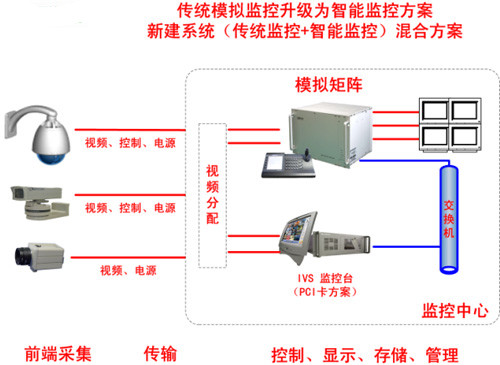
Solution 3: For the digital monitoring system of the network, select the key and high-risk monitoring targets and places, select the intelligent video server (IVS BOX) directly at the front end, actively monitor, and send the warning and alarm to the back-end management platform in real time. Quick switching and recording, the solution is as shown:
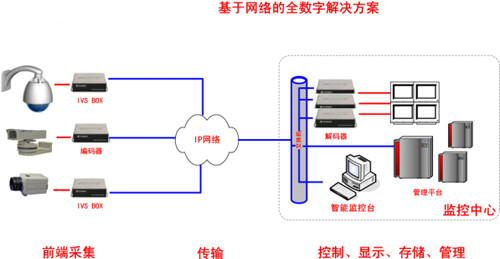
5. Top ten functions to choose from
(1) Perimeter warning and intrusion detection: Accurately detect and recognize the motion of a single object or multiple objects in a complex weather environment (such as rain, snow, fog, strong wind, etc.) and track the motion, including motion Direction, motion characteristics, etc.;
(2) Object theft or movement detection; when the objects in the surveillance scene are stolen and moved, the algorithm will automatically detect this action, which is often used for the monitoring of valuables and key equipment.
(3) Detection of legacy and abandoned items: When an object (such as a box, parcel, vehicle, person, etc.) stays in a sensitive area for too long, or exceeds a predefined length of time, an alarm is generated. Typical application scenarios include airports, train stations, subway stations, etc.
(4) Traffic statistics: Count the number of people or objects crossing the entrance or designated area. For example, for the owner to calculate the number of customers who visit their store one day;
(5) Congestion detection; identify the overall motion characteristics of the crowd, including speed, direction, etc., to avoid congestion, or to detect abnormal conditions in time. Typical application scenarios include places where people such as supermarkets and train stations gather;
(6) PTZ tracking; after detecting the moving object, the PTZ control command is automatically sent according to the motion of the object, so that the camera can automatically track the object, and after the object exceeds the monitoring range of the camera, the camera in the area where the object is located is automatically notified to continue. track;
(7) Fireworks detection: real-time detection of fireworks according to the time-space characteristics of fireworks during the occurrence of fire;
(8) Analysis of human behavior: Based on the classification of target detection, use the various behavioral characteristics of the human body to describe and analyze various behaviors, and extract dangerous and potentially dangerous behaviors such as fighting, snatching and sudden Falling into the ground, etc.;
(9) Face recognition: automatically detects and recognizes the facial features of a person, and identifies or verifies the identity of the person by comparing with the database file;
(10) Vehicle identification: Identify the shape, color, license plate number and other characteristics of the vehicle and feed back to the monitor. Such applications can be used in scenarios such as stolen vehicle tracking.
6. Looking forward to a better tomorrow
Intelligent, digital and networked are the inevitable trends in the development of video surveillance. The emergence of intelligent video surveillance is the direct manifestation of this trend. Intelligent video surveillance will change the passive surveillance of traditional surveillance and the embarrassing situation of post-recording video recording. It can provide users with more advanced video analysis functions, which can greatly improve the capabilities of video surveillance systems and enable video resources to play a larger role. The role. In order to promote the development of the intelligent video industry and achieve multi-win results, Tianjin Tiandi Weiye Digital Technology Co., Ltd. will continue to exert its strong advantages in the traditional monitoring field, and actively develop and improve the emerging intelligent monitoring system so that the two can fully utilize their respective The advantage is to create a comprehensive solution that meets the needs of end users.
Socket With Bluetooth Audio Play is a multi-function power strip, TOUKOO patent product.
With two Bluetooth speakers, you may play music from each of your mobile devices.
AUX interface provides an option to connect your desktop as well, like all other ordinary speakers. SB ports power strip provides convenient charging for mobile devices.
PC/ABS flame retardant, phosphor bronze+pure copper.
Bluetooth or AUX connection loudspeakers 8Ω impedance.
Socket With Bluetooth Audio Play
Socket With Bluetooth Audio Play,Usb Ports Power Strip,Extension Socket With Bluetooth Speakers,Electric Outlet With Bluetooth Speakers
ZhongShan JITONGLONG Plastic Hardware Co. Ltd. , https://www.toukoo-electronics.com